The CFAA: Where to draw the line?
The imprisonment of Andrew Auernheimer (A.K.A. weev) and the death of Aaron Swartz have lead to many public discussions, as were both being prosecuted under the Computer Fraud and Abuse Act. The CFAA is also being used civilly by nefarious groups like Prenda Law to attempt to find methods of attaching liability to IP addresses, essentially for "accessing computers without authorization." While the EFF has focused their attention on the cases of Auernheimer and Swartz, a large protest has begun against the CFAA, or how it is now being used.
There is a clear divide in these suits and actions taken by prosecutors. I believe that the CFAA as it is applied now, is unconstitutional as it leads to a position where there is no definite or certain "line" that needs to be crossed on a computer in order to have it be a criminal act. Because there is no definite line, the CFAA is unconstitutionally vague and leads to a position of selective enforcement.
The CFAA and Weev's Case
Before I get into Weev's AT&T "hack" I must confess that I have known of Mr. Auernheimer for nearly 12 years, but I am not biased for or against him based on that relationship. That part out of the way, his case is the perfect case to show where the line should be not drawn in the sand. Weev's "hack" of AT&T came from requests to a public webserver, which allows public access. They allowed this access to personal information to anyone who knew the address to type into a web browser. This information was made PUBLIC by AT&T by their failure to secure their systems.
This is not to say that any entity in particular has a duty to prevent intrusion, but there is a difference between intrusion and opening a public web address. If no password is required, the request should not be considered an intrusion. If no security is in place, the request should not be considered an intrusion. If a person is not seeking to gain different or higher ranking credentials on a computer within a web request, this should not be considered an intrusion.
How is this activity different than what SHOULD be a violation under the CFAA? Let us hack my office and see.
CFAA and my Office
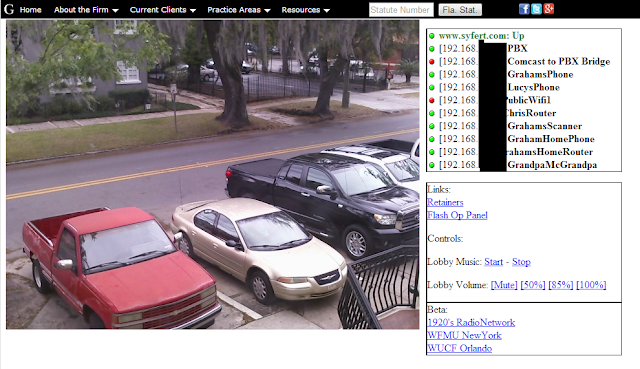
At my office, I have a webcam setup for security on a tiny linux box at the front of my office. The page for the webcam gives me the status of certain servers and devices that I run using ping or curl.
The page for this webcam setup is a public webpage, and there is no password to access this particular page. It is a secret known only to me, not available in any google search, but if you knew to type in the URL the public at large would be able to access it. If someone was lucky enough to find the publicly accessible portion of this page, which is everything to the right of webcam picture, then they could have certain control over my office. However, there is a password on the webcam stream, and so the image would not be accessible.
Over to the right hand side, there are also controls for the lobby music. Again, these are publicly available controls. You can turn the lobby volume up, turn it down, change the channel. stop it, start it, etc. If you found this particular page, without a password, you would be able to create some havok in my lobby. You would probably not be able to use this information in anyway, but it is a control of a device through the internet.
If someone found this webpage, and spent all day turning the music in my lobby up and down, and switching stations, I would be very annoyed and angry, but this would be my fault.
CFAA is not a license to be insecure
Now, imagine that weev found my webcam control page, and started spending a lot of time changing my lobby music at random (which is not all too far fetched). I would and should have no recourse against his actions. While it was not expressly permitted by me, by putting this control on the World Wide Web, unpassworded, I have opened it up for the world. I do not need to list it with google, I do not need to share the URL. If it happens that the URL is hit, then the URL is hit. Again, I should have no recourse.
Now imagine that weev started saying things to me like, "Hey man, nice suit. Jerk face." and started saying that he could see me walking into my office. Well, to access that particular part of the webcam, the video stream, he would need to get around the password screen that pops up when the page is opened. This is a line that shouldn't be crossed. For the bar exam, one of the things we always had to remember for Burglary was that at common law, it was "Entering the dwelling house of another" and "at night" and "with the intent to commit a felony" but we have no such straight principles within the CFAA.
This lack of bright-line rules within the CFAA and a lack of understanding of technology (or a lack desire to understand) on behalf of some members of the judiciary, leads to a position where the knowledgeable prosecutor can pull the wool over the courts eyes.
Part of the lack of bright-line rules comes from the inherent problem of accurate language required by statutory construction paired with a lack of understanding and fear of technology. And, lets face facts, the common law does not exactly seem to apply nor basically even shed light on the issues presented by technology. The law of trespass has been used to describe entry upon land for centuries. States have instituted laws regarding the posting of signs regarding trespass. There is no "Signpost" on a webserver where such trespass warnings can be instituted. There are only password prompts or denials of access. It is not the "World Wide Web" of secrets, it is a world wide web of publicly accessible information with nests of secrets all around. If you want your information to be secure, and for a potential intruder to be criminally or civilly culpable, then it is your duty to put up sign posts or passwords, no matter how simple. Access to this information should be restricted, and secured, so that actual intrusion becomes necessary to get at the information.
If I place upon my server a public directory, lets say http://www.syfert.com/AB34392DQERE3, it is a good chance that this would never be guessed. But if I start throwing information into that folder without placing passwords on the information and someone accesses it, it is my fault. I put the information on the web. But, if I went to a judge or a prosecutor and claimed that you accessed that directory without permission and gained valuable information, I might be able to get them to run with it. If the Prosecutor or Law Enforcement had some particular reason to hate you (i.e. you are very vocal in a political party or movement or just being a general jerk like Weev) then they would spin the story into a security breach and seek punishment. The lack of direction within the CFAA and the lack of understanding of technology have lead to the perfect storm of selective enforcement of the law.
TAKE ACTION TODAY https://action.eff.org/o/9042/p/dia/action/public/?action_KEY=9005

I really enjoyed reading this blog post.
ReplyDeleteThe ideas were explained clearly and were easy to understand. I liked how the content stayed focused and well structured. It made the reading experience smooth. Overall, a very pleasant read.